Data breaches and identity theft are rampant nowadays, making the proper handling and disposal of confidential and sensitive information critical. Document shredding and electronics destruction services play a vital role in protecting confidential data. However, ensuring the security of your documents and electronics from the moment they leave your possession until they are destroyed requires a meticulous process known as the chain of custody. This procedure guarantees that every step in the destruction process is accounted for, minimizing the risk of information falling into the wrong hands. In this blog, we’ll explore why the chain of custody is important and how it safeguards your business and personal information.
What Is Chain of Custody?
Chain of custody refers to where documents and data are at every stage of their lifecycle, from when the document was created to its destruction. In general, chain of custody provides a paper trail for your documents. It’s a form of confirmation that your documents were shredded and recycled. In addition, this process ensures that your materials are managed at every step to prevent unauthorized access, loss, or theft. This chain of custody ensures accountability and security, making it a critical component of effective document and electronics destruction services.
Why the Chain of Custody is Important
A chain of custody process for document shredding and electronics destruction is essential for businesses that receive certified shredding services from a shredding company. Getting a secure chain of custody from a shredding company is important for many reasons, which include:

Enhanced Security: The chain of custody provides better security by maintaining strict oversight of documents throughout their lifecycle. Through this process, businesses can prevent unauthorized access or potential data breaches. Each step involved in a chain of custody is carefully monitored and documented to ensure your sensitive documents are controlled.
Legal Compliance: Many industries are governed by strict regulations regarding how sensitive information is handled and destroyed. Receiving a well-documented chain of custody can help your business comply with HIPAA, FACTA, and other privacy legislations. They require proof of secure data handling.
Proof of Destruction: At the end of the shredding process, your business will receive a certificate of destruction. The certificate provides detailed information about the shredding process and proves that the documents have been destroyed in compliance with the law. During audits and legal inquiries, it’s crucial to demonstrate this certificate as proof that your business has responsibly managed its data destruction.
Prevent Information Theft: Identity theft and data breaches are prominent business problems. Therefore, properly destroying sensitive documents is more important than ever. A chain of custody can ensure that your documents are not only shredded but handled to minimize these risks.
Efficiency and Reliability: A chain of custody provides a layer of efficiency and reliability to your destruction process. As a business, you can rely on systematic procedures and ensure your documents are handled consistently.
The Key Components of the Chain of Custody
Each element of a chain of custody is designed to ensure that your sensitive documents are handled securely from start to finish. When you off-site your materials to a destruction company, there are key components to the process that make it valuable for businesses looking to keep in compliance.
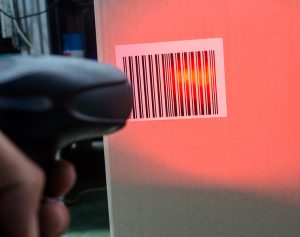
Barcode Tracking: Your boxes are assigned barcodes scanned at various points throughout the handling process to create a traceable record. This record details when your documents are picked up, transported, and eventually shredded.
Locking Shred Bins: Secure shredding bins protect the documents from being tampered with and accessed until they are shredded. These bins remain locked until they’re ready to be shredded, ensuring that your documents are protected from unauthorized access throughout the process.
GPS-Tracked Trucks: Many shredding companies use trucks equipped with GPS tracking to monitor their location in real time. GPS tracking ensures that the documents are transported securely and allows you to track the exact route taken to the shredding facility.
24/7 Video Monitoring: Many shredding facilities have video surveillance to record shredding activities. The footage serves as additional proof that the materials are handled securely and shredded.
The Chain of Custody Process
Chain of custody is crucial for businesses that must protect confidential information from unauthorized access and potential misuse. During the destruction process, every action taken before the initial shredding is meant to demonstrate this process. Furthermore, it’s to ensure compliance with legal requirements and provide assurance that all sensitive, outdated data is destroyed.
A Detailed Step-by-Step Chain of Custody Process
- Secure Collection: Start by placing documents or electronics into locked shredding bins provided by your service provider. These bins are designed to meet required security standards, prevent unauthorized access, and are stored in secure areas.
- Document Barcoding: Each bin is assigned a unique barcode for tracking purposes. These barcodes are scanned at various points throughout the process, ensuring a clear chain of custody and allowing you to monitor the status of your items.
- Secure Transportation: When the bins are full, trained personnel collect them. During transport, the bins remain locked and are loaded onto GPS-tracked trucks, enabling real-time location monitoring for enhanced security.
- Arrival at Shredding Facility: Upon arrival at the shredding facility, the bins are scanned again to update their status in the tracking system, confirming their arrival without any breaches.
- Controlled Shredding: The locked bins are then moved to a secure area, where they are emptied directly into industrial shredders. The destruction process is conducted under 24/7 video surveillance, ensuring all actions are recorded and available for review if necessary.
- Recycling of Shredded Material: If the facility follows environmentally sustainable practices, the shredded material is compressed and sent to a recycling center after destruction.
- Certificate of Destruction: Once the shredding process is complete, a certificate of destruction is issued. This certificate provides details of the chain of custody, including timestamps, locations, barcode numbers, personnel involved, and other relevant information, serving as proof that the items were securely destroyed according to requirements.
Ensure a Secure Destruction Process with Shred Nations
Secure document shredding and electronics destruction with a verifiable chain of custody can protect your business from potential risks. For more information on how to start securing your disposal process, contact Shred Nations. Call us at (800) 747-3365, fill out the form, or contact us directly using our live chat. We’ll get you free quotes on secure destruction providers near you.