
We spend several hours every single day on our phones where much of our lives is documented, recorded, and kept accessible to us at all times.
While the power of having everything you need readily available at your fingertips at anytime is convenient and efficient, if lost or stolen cell phones quickly compromise our personal security.
People often go to great lengths to protect personal information stored on their desktop computers, laptops, or contained in physical documents, however that level is care is rarely taken when it comes to protecting information stored on cell phones.
Watch the video or read the transcript below to learn about one of the best ways to protect the information on your device: absolute physical destruction.
Video Transcription
Understanding the Risks From Old Cell Phones
Most people understand the importance of protecting things like social security and credit card numbers, but they often overlook how much of that information is stored on their cell phones.
Cell phones are gold mines filled with personal information, and if identity thieves get one before the old phone is destroyed it can lead to financial consequences.
Why It’s Important to Destroy Old Cell Phones
Thieves don’t need your credit card numbers to steal your identity any more—instead a new and growing threat to consider is account takeover fraud.
Cell phones hold information ranging from our emails to various accounts, passwords, and other personal information, making it essential that old phones and the information they contain are properly destroyed before they’re disposed.
Account Takeover Fraud by the Numbers
 To put the risk of not destroying old cell phones in perspective, there has been a significant rise in account takeover fraud in the last several years—in 2019 costing an estimated $16.9 billion.
To put the risk of not destroying old cell phones in perspective, there has been a significant rise in account takeover fraud in the last several years—in 2019 costing an estimated $16.9 billion.
With the number of account takeover fraud cases tripling as well, it’s likely a sign that the importance of protecting the personal information on cell phones will only continue to grow.
How to Destroy Cell Phones
There are several methods used for destroying old cell phones like destruction or demanufacturing and degaussing, however some options provide more benefits than others.
Finding the Best Destruction Method
Cell Phone Shredding
Shredding is the easiest and often cheapest method. It doesn’t require manual data wiping, separation of components, and most shredders also take care of electronics recycling afterward.
Cell Phone Demanufacturing/Degaussing
Demanufacturing/degaussing is a slower process because it does require phones to be manually dismantled piece by piece. It also is typically done by trained specialists, adding to potential cost.
DIY Destruction
The fastest approach is smashing or destroying by yourself. However, EPA hazardous waste laws prohibit throwing the pieces in the trash—instead recycling (and potential cost) is on you.
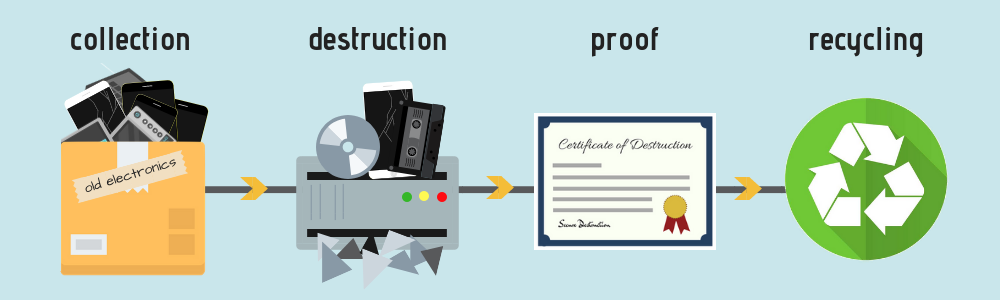
The Cell Phone Destruction Process
- Destruction providers start by collecting yours and other cell phones, hard drives, and various electronics from other customers for shredding.
- Next the electronics are loaded into an industrial shredder where they’re broken into unrecoverable pieces.
- After shredding you’re provided a certificate of destruction, detailing the time, date, location, and the chain of custody for your cell phone’s destruction.
- Finally the cell phone pieces are recycled according to EPA and state hazardous waste laws. With cell phone shredding, recyclers can get the maximum value form the metals used in electronics.
Need to Destroy Old Cell Phones?
Shred Nations partners with secure electronics destruction service providers across North America. We can help you find a destruction solution to protect the information stored on your mobile device.
Give us a call at (800) 747-3365, fill out our form, or contact us directly using our live chat for free and customized quotes on secure destruction services near you.












