
Every year, the threat of identity theft continues to grow. With advancements in technology come undiscovered vulnerabilities that allow fraudsters to get their hands on your personal information and new theft tactics are employed as they are created.
Unfortunately, identity thieves can use as little information as your full name and home address to start abusing your identity and reaping costly benefits at your expense.
Types of Fraud and Identity Theft Risks
Every year new and different fraud strategies emerge. With new technological advancements such as smart homes, wearable devices, voice operated devices, and more, there are evermore ways to exploit people’s privacy.
Common fraud tactics that exploit modern technology include:
-
- account takeover fraud
- social media data exploitation
- card-not-present fraud
- using false SMS text message prompts for password and account login information
- synthetic ID theft
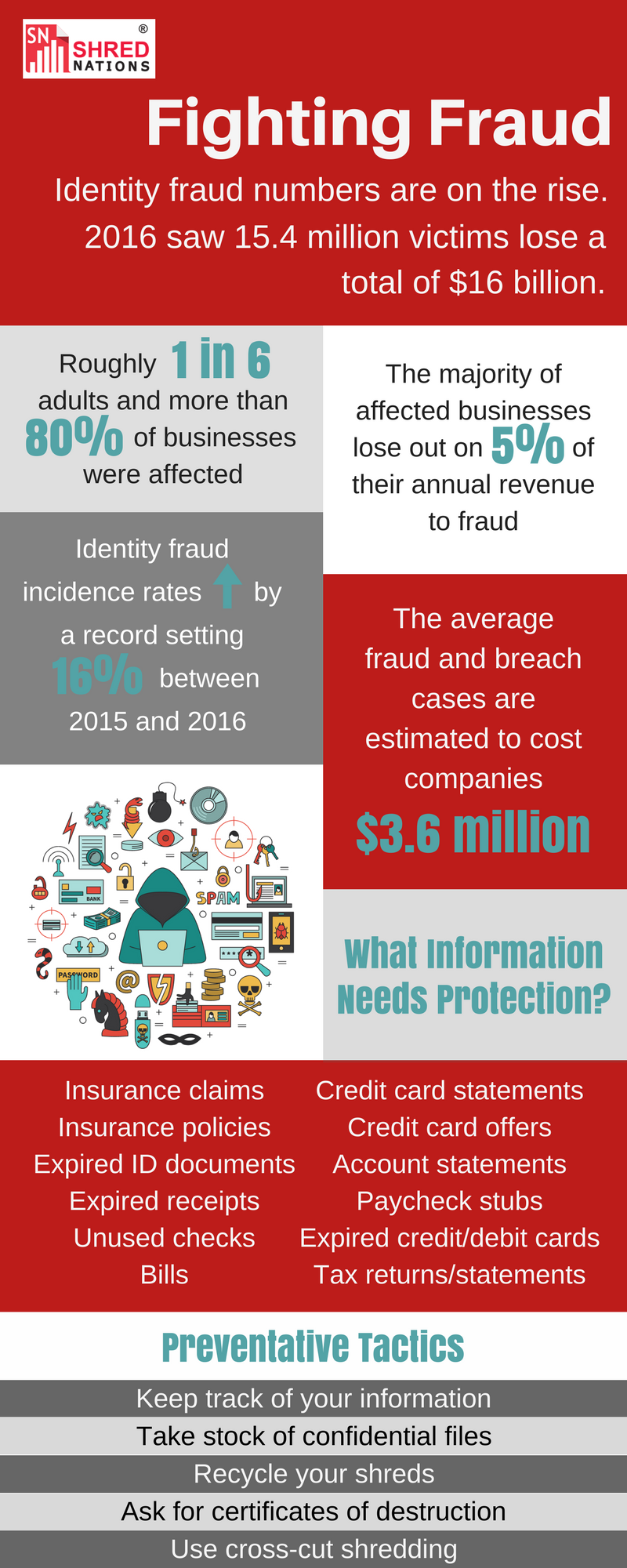
Identity Theft by the Numbers
While fraud and identity theft is not a new phenomenon, the digital world has created a massive environment where anonymity is prevalent—creating a perfect breeding ground for identity theft.
Comparing the numbers overtime it is clear that even in just the past few years the number of identity theft cases have steadily increased.
-
- In 2014 there 12,700,000 Americans were victims of identity theft
- In 2015 there were 13,100,000 American victims of identity theft
- By 2017 the number of Americans impacted by identity theft rose to 16,700,000
As the reports of identity theft continue to rise, the issue of privacy and information security has grown in import.
Safeguard Your Identity
There are a number of steps you can take to ensure that you do not become a victim of identity theft, including remaining cautious of the people and businesses that you are sharing your personal information with and shredding any documents containing confidential information.
Avoid Identity Theft by Shredding Your Confidential Data Today!
Falling victim to identity theft can cost you both time and money that you may not be able to afford. Shred Nations partners with a nationwide network of shredding contractors that can handle any documents or devices containing your personal information.
For a free quote on data destruction services in your area, simply fill out the form to the right or give us a call at (800) 747-3365.
Within minutes of speaking with one of our experts, you will receive quotes from contractors in your area that will work diligently to complete your service at an affordable price.












